Sample Report
Info-Tech’s Security Effectiveness Reports are designed to apply to all organizations, regardless of size or industry. Download a preview of these reports to see the value they can bring to your organization.
Improve security effectiveness by harnessing the wisdom of your team.
No one knows your organization’s security processes and technologies better than your IT team. Info-Tech’s Security Effectiveness reports let you leverage the collective knowledge of your staff to enhance security effectiveness in the area (or areas) you’d like to focus on. Use these reports to optimize policies and processes, drive improvement in technology usage and decisions, and facilitate alignment, consistency, and knowledge transfer among your team.
Info-Tech’s Security Framework Model is derived from COBIT and TOGAF, two globally accepted frameworks used by businesses to optimize the value of IT. Security Effectiveness reports are available in the following security areas:
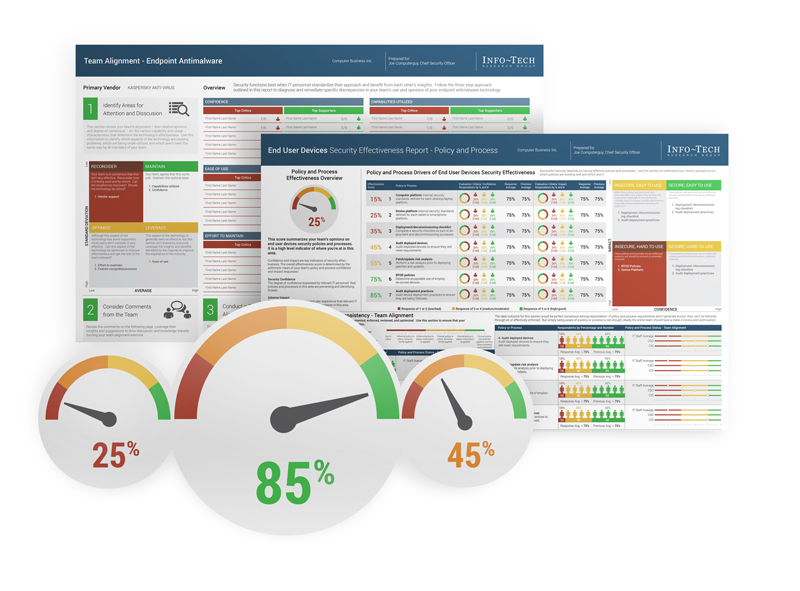
Contains all the information you need to standardize your approach and ensure optimal value from each of your technologies: specific items for attention or discussion, areas to potentially reconsider, opportunities for knowledge transfer, and comments to consider from your team.
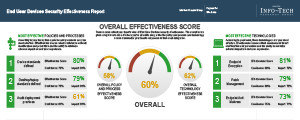
Info-Tech’s Security Effectiveness Reports are designed to apply to all organizations, regardless of size or industry. Download a preview of these reports to see the value they can bring to your organization.